SSL/TLS handshake: the detailed process and how it works
SSL/TLS handshake is the process of establishing a secure connection between a server and a website.
SSL certificates or digital certificates have become popular because of their security for web users, website owners and publishers. They use public key cryptography to encode the transfer of data between the client and the web server. There are various types of digital certificates, but all serve the same process of providing security for both the client and the web owner.
Web owners often use SSL certificates to prevent hacking. To begin a secure connection, both the client and server first perform the SSL handshake process, which includes authentication, key exchange process, etc. Let’s start with SSL/TLS certificates and understand how they work. Then we will explain the entire TLS handshake process.
What is SSL/TLS?
SSL (Secure Sockets Layer) is a standard security protocol widely used to protect communications over the Internet. SSL uses [asymmetric encryption](https://www.ssl2buy.com/wiki/symmetric-vs-asymmetric-encryption-what-are- differences) to protect information from attackers. SSL certificates are issued by trusted certificate authorities to ensure that no one (without the correct encoding/decoding key) can read the data shared between the user and the server.
SSL certificates perform the process of encryption and decryption with the help of two keys. One is a public key that can be used by anyone trying to establish a secure connection to the site. The other key is a private key hidden by the web server and is used to decrypt messages received from the client. In this way, a secure connection is established between the server and the client’s browser.
If you visit a site that does not have an SSL certificate installed, all information is shared in plain text, which means that anyone can intercept and read your private data. Hackers can use this information for their malicious purposes.
SSL certificates provide security against these attacks. Even if someone can capture the data, he/she will not be able to read it without the correct encryption/decryption key.
Compared to SSL, TLS (Transport Layer Security) is the advanced version. Nowadays, almost all websites use TLS instead of SSL because it provides better protection than SSL.
You may be confused as to why we still use SSL more commonly than TLS. it’s like a brand name that has caught on in the marketplace. This means that if you purchase an SSL certificate, you do not need to purchase a TLS license.
What is the SSL/TLS handshake?
The SSL/TLS handshake is the process of establishing a secure connection between a server and a site. It is one of the most critical steps in establishing a secure connection. Once a secure connection is established, both the server and the client can communicate with each other with confidence.
The SSL handshake process accomplishes three main things.
- negotiate the cipher suite
- authenticate the browser and the server.
- exchange keys
Let’s explain them one by one.
Negotiation of cipher suites
A cipher suite is a set of instructions that focuses on ways to provide security to the network. It provides a set of guidelines on how secure data can be communicated with HTTPS, FTPS and other network protocols.
Browsers may vary from a specification perspective, such as Mozilla Firefox, Safari, Chrome, and Microsoft Edge. similarly, common operating systems such as Apple macOS, Microsoft Windows, Linux, and Android iOS have slightly different support for server-side functionality. All of this becomes more complicated when you introduce custom settings.
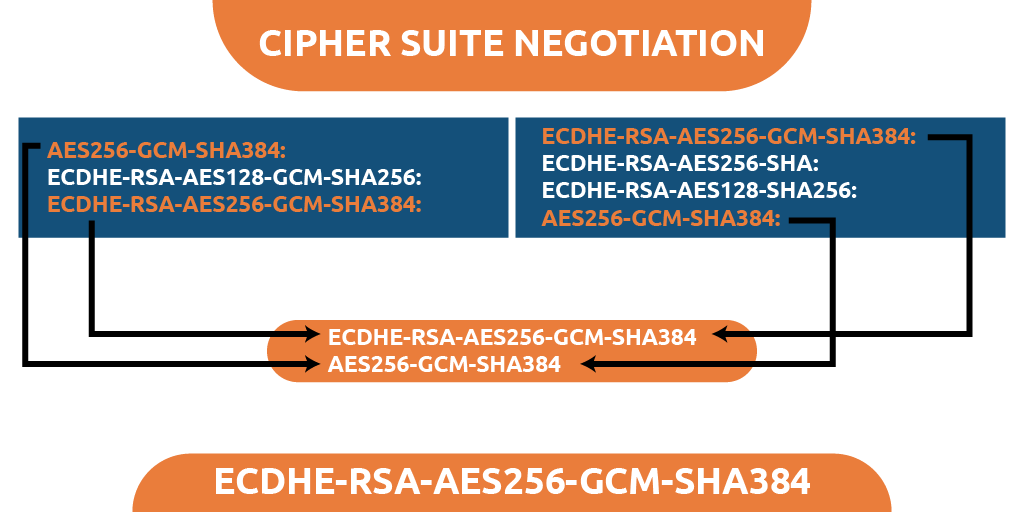
Thus, the first phase of the TLS handshake allows users and servers to share their resources so that they can identify the encryption features they jointly support.
Once the browser and server have identified a specific encryption policy, they use it to provide the SSL license to the user. This is called a cipher suite.
Authentication
Once the license is received, the client’s browser will investigate to ensure that the certificate is “authentic”. Not only do you need to encode the information to get the secure link; you must also ensure that it is submitted to the appropriate website/organization. But the way they implement it depends on the cipher suite used.
All trusted SSL certificates are granted by authorized digital certificate authorities Certificate Authorities (CAs). These companies need to follow strict issuance and certificate protocols in order for the licenses they grant to be approved. This is primarily to ensure that you only get certificates for domains or businesses that you own. In this way, you can assume a CA, such as a notary public. The signature indicates that the person or organization on the license is who they claim to be.
The client performs multiple cryptographic security tests throughout the authentication process of the TLS handshake to ensure that the license submitted by the server is legitimate. This involves verifying the digital signature and ensuring that a trusted CA has granted the certificate.
At this point the user also confirms that the server has the private key associated with the certificate. All SSL licenses use a key pair containing a public key and a private key. The public key is used to encrypt the data, while the private key is used to decrypt it. This is called “asymmetric encryption” because a separate key is used to accomplish the task.
The client can use the public key to encode random messages to create session keys using the most popular public key cryptosystem, RSA. The server can only decode and use the message if it has the private key to ensure proof of ownership.
Key Exchange
The final part of the process includes the generation of the “session key”, which is the key to the secure interaction that will eventually be exploited.
Session keys are “symmetric”, which means that the same key is used for encoding and decoding. These keys are more effective than asymmetric keys in achieving effective encryption and are therefore ideal for transferring data back and forth over HTTPS links.
Depending on the cipher suite chosen, the exact method of creating the key will vary; [RSA and Diffie-Hellman](https://www.ssl2buy.com/wiki/diffie-hellman-rsa-dsa-ecc-and-ecdsa-asymmetric-key- algorithms) are two popular methods.
Each party notifies the other that they have done all the relevant work to complete the handshake, and then both parties perform a checksum to ensure that the handshake is free of any intentional interference or fraud.
In an HTTPS link, this is the first stage that must occur, even before the site is accessed. This TLS handshake process occurs in a very short period of time.
Once the SSL handshake is complete and all information transmitted and obtained between you and the server is secure, the encoded and authenticated HTTPS link is initiated.
SSL/TLS Handshake: Step-by-Step
Depending on the type of key exchange method used and the mutually recognized cipher suites, the exact stages in the TLS handshake may vary.
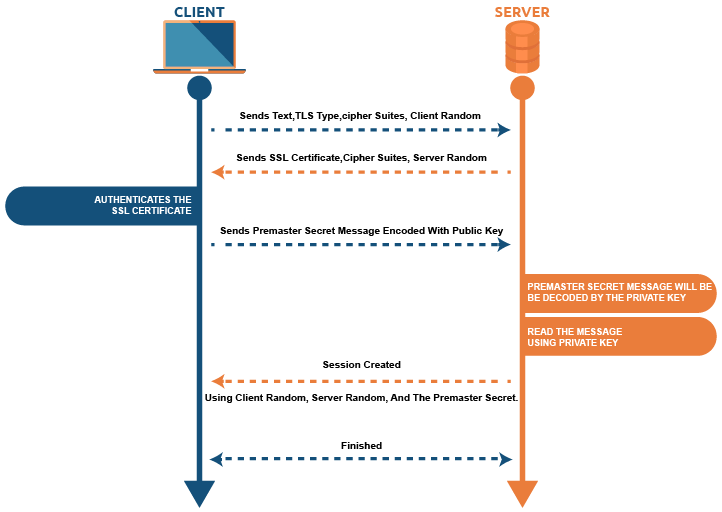
The user starts the handshake process by sending a “Hello” message. This message contains the TLS type and cipher suite supported by the user. It also includes a string of arbitrary bytes called “client random”. 2.
In reply, the server sends a text with the SSL certificate. The text also contains the cipher suite chosen for this process and a random string of bytes generated by the server called “server random”. 3.
The user’s browser verifies the SSL certificate provided by the server and the certificate authority that issued it. This proves that the server is what it says it is, and that the client is interacting with the licensee. 4.
4. The client sends another message (premaster secret) encoded with the public key of the SSL certificate, which can only be decoded by the private key held by the server.
5. The server reads the message using its private key. 6.
6. After this, the session key is created using the client random, server random and premaster keys. 7.
7. Both the server and the client send a “done” message, encoded with the session key. 8.
8. The SSL handshake completes successfully and both parties continue secure communication using the session key.
Conclusion
The TLS/SSL handshake is one of the fundamental processes used to secure Internet communications. It happens quietly and quickly behind the scenes, without most people knowing about it. But without its successful implementation, user data and client resources are at risk of being hacked. the SSL handshake process depends on the client and server selecting the correct cipher suite and SSL/TLS version to initiate the process. Read the full guide, as described above, for a clear understanding of the SSL/TLS handshake process.